SkyLift WiFi Gelocation Spoofing Device
SkyLift works by broadcasting MAC addresses that are associated with WiFi routers in a different location. WiFi geolocation services rely on the assumed stable location of home and commercial routers to return accurate geolocation information. Because space-based GPS signals are attenuated in dense urban areas, WiFi became a viable alternative for location services in consumer tech. However, it's also vulnerable to spoofing attacks as discovered by researchers at ETH Zurich/Swiss Federal Institute of Technology in 2008.
Ten years later WiFi geolocation spoofing, surprisingly, still works.
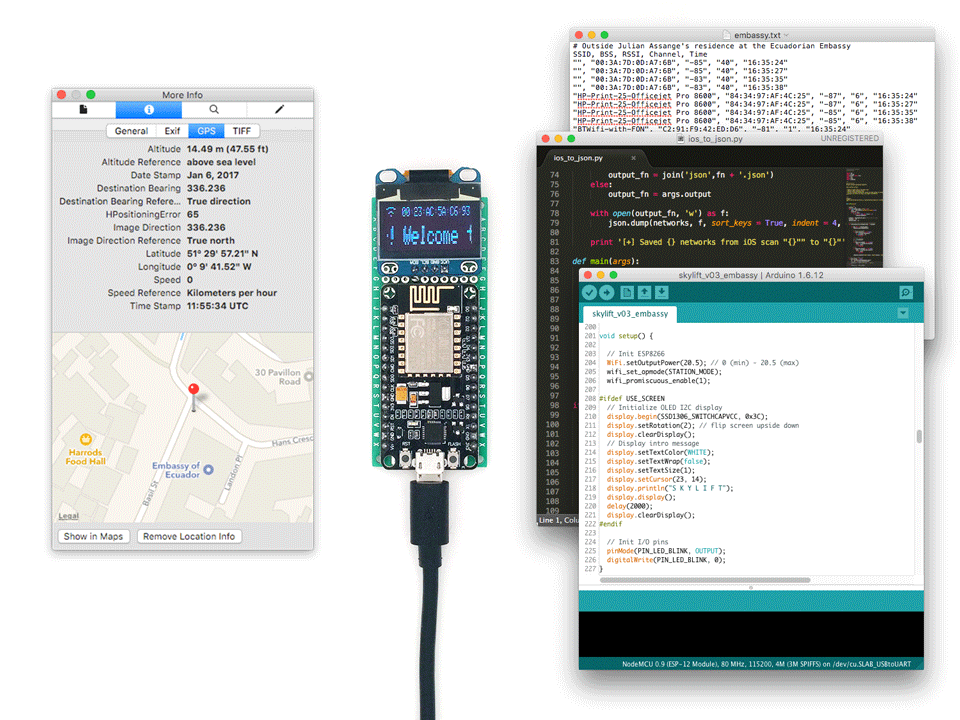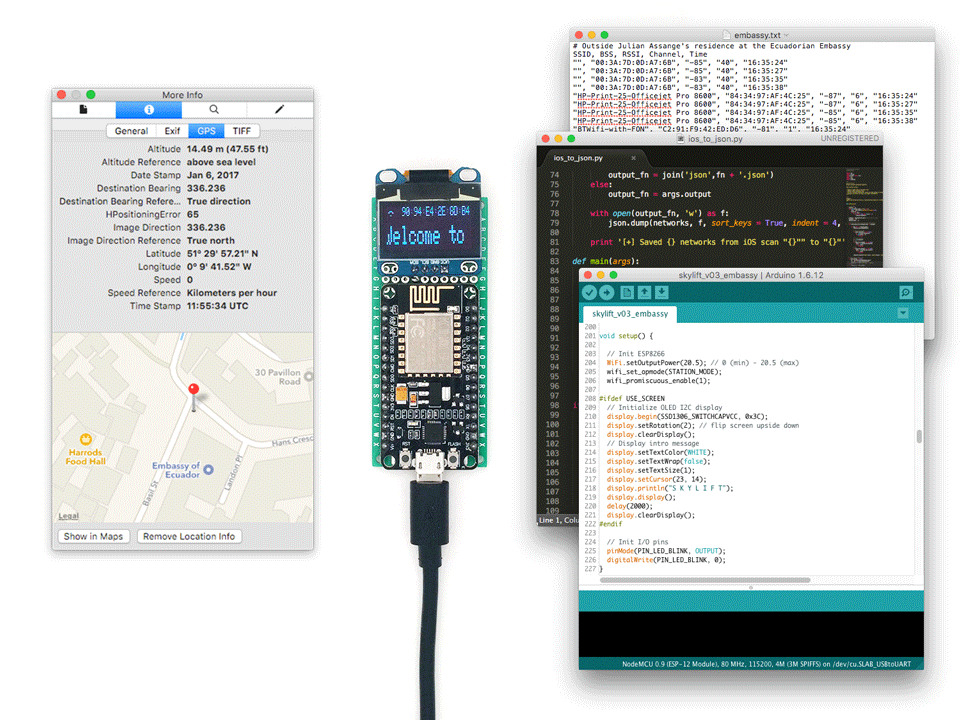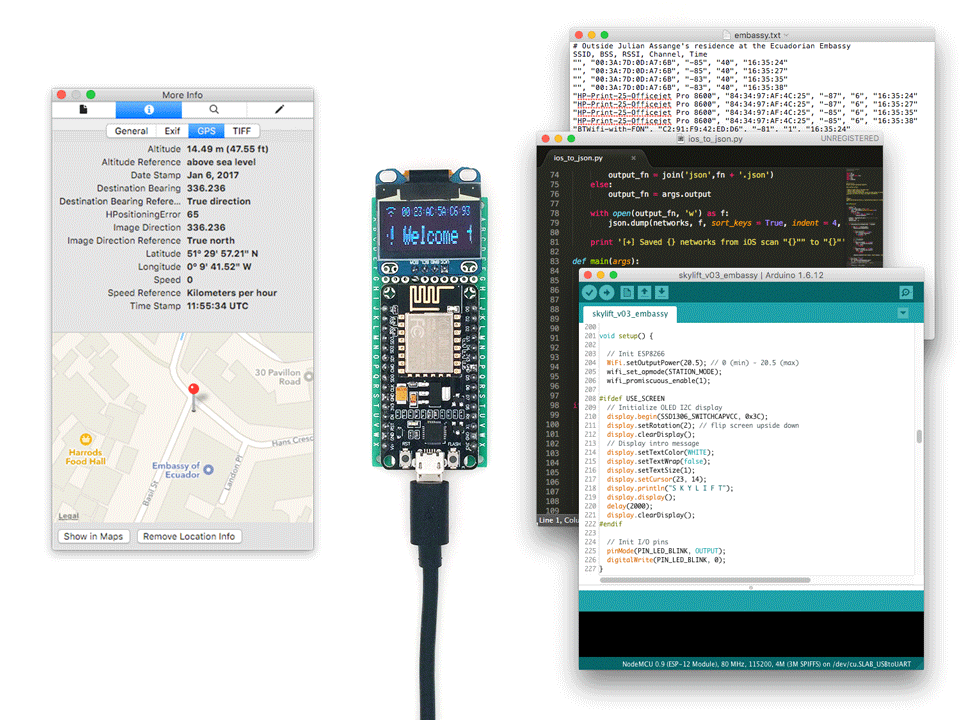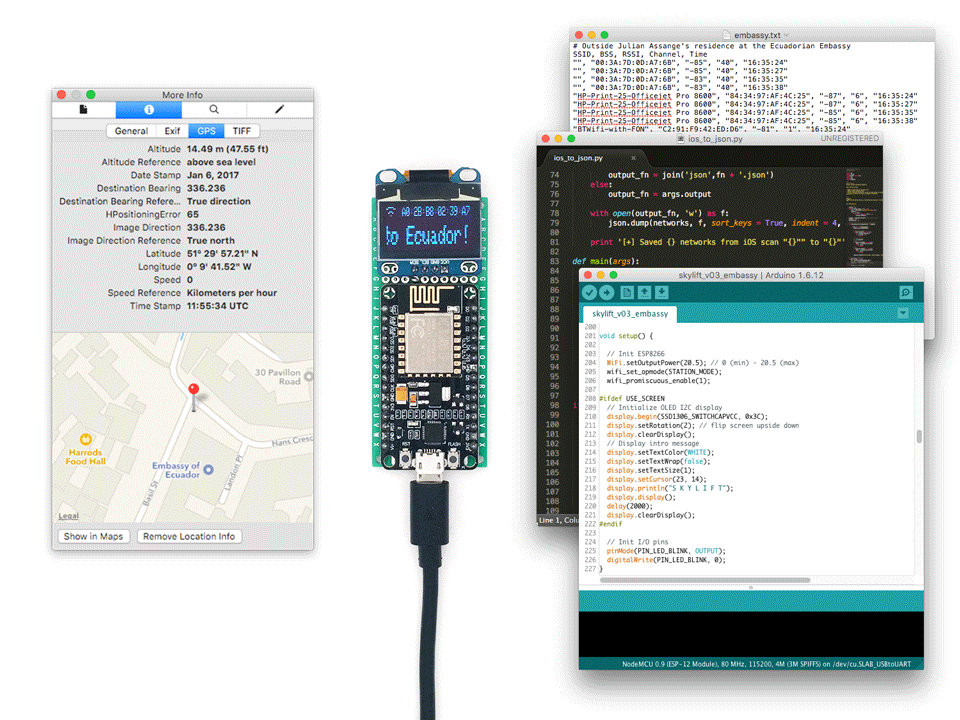
Made for !Mediengruppe Bitnik’s Assange Room. Developed in collaboration with Surya Mattu
SkyLift is a WiFi geolocation spoofing device that virtually relocates visitors to Julian Assange’s residence at the Ecuadorian Embassy in London. The device was made for !Mediengruppe Bitnik’s Assange room and works by broadcasting WiFi signals (beacon frames) that exploit WiFi geolocation services.
Thanks to a web-residency grant from Schloss Solitude SkyLift now runs on the ESP8266, a low-cost Arduino-compatible WiFi microcontroller, and is open source. Full code and documentation on https://github.com/adamhrv/skylift.
Previously, this technique would require a small linux computer, USB WiFi dongles, and a program such as mdk3 to broadcast beacon frames with custom MAC addresses. This was functional but less practical. The small size and low cost of the ESP8266 microcontroller offers new possibilities for creative geolocation spoofing.
How it Works
To get started you can follow the instructions on https://github.com/adamhrv/skylift and use the provided beacon frames to virtually relocate your smartphone to Julian Assange's residence in London. Once successfully relocated, every app on your phone will think you're standing outside 3 Hans Crescent, London SW1X 0LS, even FindMyPhone and Pokemon.
If you'd rather go somewhere sunny, record your own locations using the instructions on GitHub.
SkyLift only relies on broadcasting MAC addresses. There is no IP spoofing, no GPS signal spoofing, no VPN, and no 3rd party app involved. It works for any app on your phone with location services available, including FindMyPhone (iOS) and Pokemon. It works without connecting to any WiFi network. However, it only works when you have WiFi location services enabled. And typically works best indoors (where GPS is attenutated) and in locations where nearby WiFi signals are less than -80dBm.
For a more thorough technical overview about how Beacon Frames work and the basic WiFi protocol information visit PacketBridge (2012), an earlier project from the Critical Engineering group using the same technique, or view the README on https://github.com/adamhrv/skylift.
Project Timeline
- Summer 2018: DIY PCB kit in progress for workshop in Berlin
- May 2017: Interview with Schloss Solitude https://schloss-post.com/the-future-of-living-with-surveillance/
- May 2017: Code and build instructions on https://github.com/adamhrv/skylift
- January 2017: Version 0.2 exhibited at La Gaîté Lyrique and FACT Liverpool.
- April 2016: Version 0.1 exhibited Zoo Galerie in Nantes, France.
- August 2015: Research and development of proof of concept: Surya Mattu (US) suryamattu.com

Prototyping with various WiFi devices. Photo: Adam Harvey
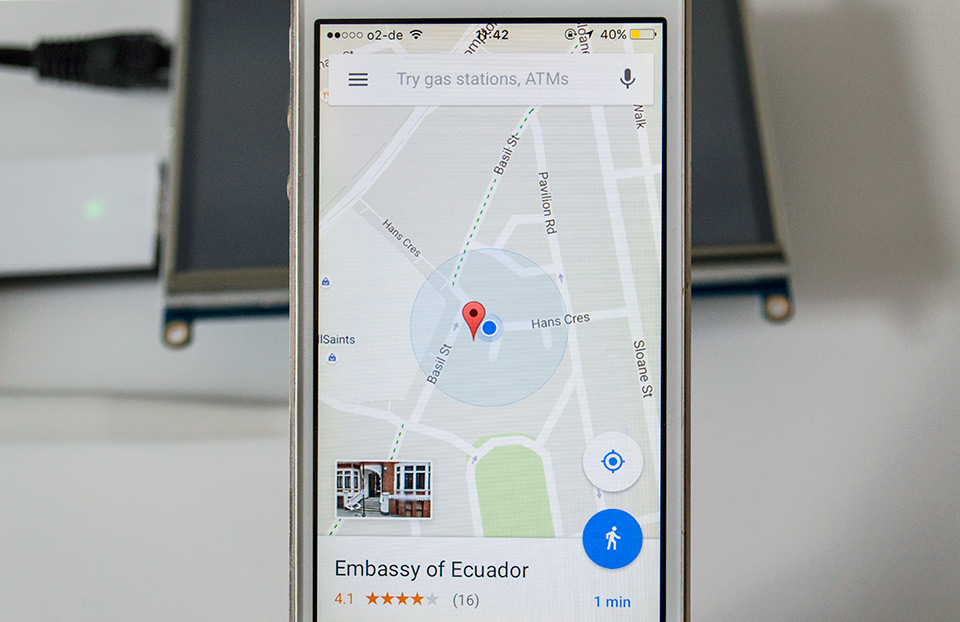
Emulating the Ecuadorian Embassy from within Germany. Photo: Adam Harvey
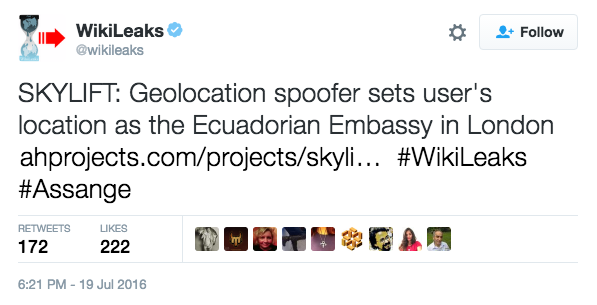
Tweet from Wikileaks | source

Collecting data in London. Photo: !Mediengruppe Bitnik
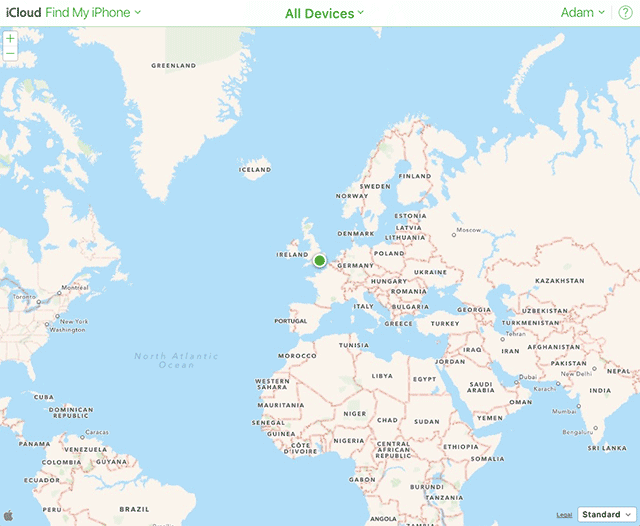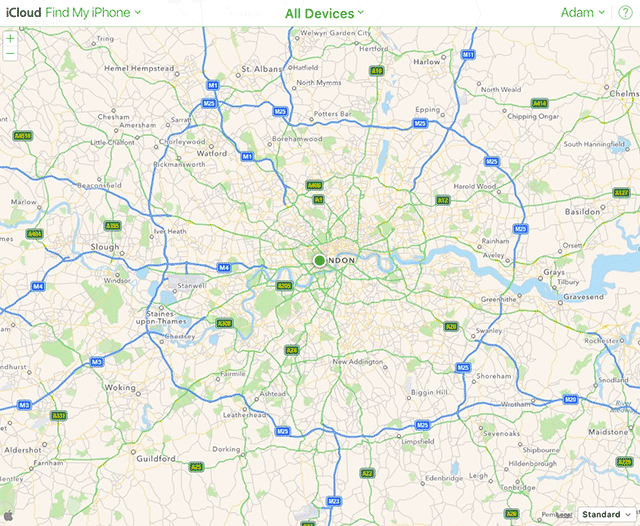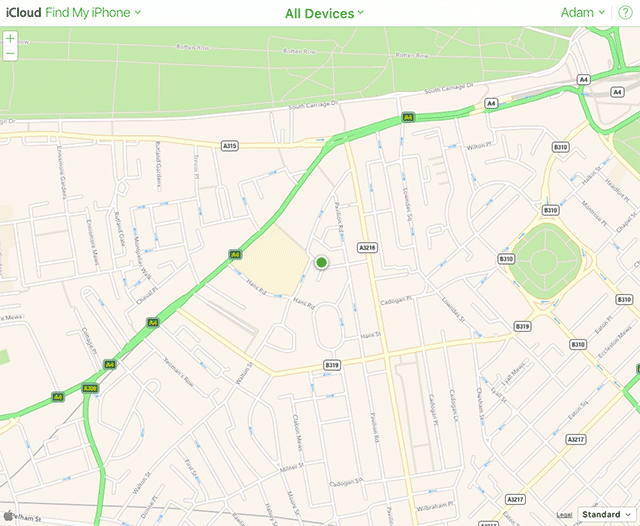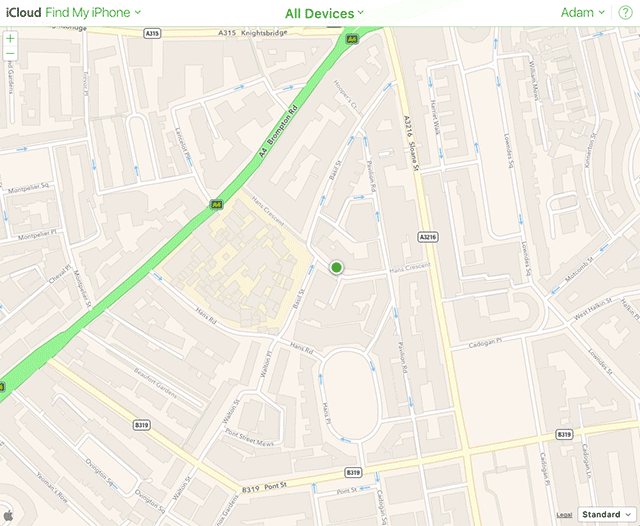
Also works with FindMyPhone (iOS). Adam Harvey
Credits
- Version 0.3 made with support from a web residency with Akademie Schloss Solitude & ZKM
- Version 0.2 made with support from exhibitions at La Gaîté Lyrique and FACT Liverpool.
- Version 0.1 made with support from Zoo Galerie in Nantes, France.
- Research and development of proof of concept: Surya Mattu (US) suryamattu.com
- Concept in collaboration with !Mediengruppe Bitnik
- Technical advisement from Julian Oliver (DE) julianoliver.com | packetbridge
- Research assistance and Python development contributions by Leon Eckert (US/DE)
Citations
- Location Spoofing Possible With WiFi Devices (2008)
- PacketBridge (2012)
- How to Spoof Wi-Fi Geo-location (2013)
- Don’t Trust Geolocation (2013)
- Spoofing WiFi AP Based Geolocation (2013)
Resources
- Beacon Frame Overview
- Beacon Frame Packet Structure
- Geolocation API by LocationAPI
- Geolocation API by Google
- https://mitmproxy.org/ use this to inspect where BSSIDs are being sent
- Interesting paper on carrying out a targeted attack using WiFi Geolocation Spoofing
- Using mdk3 in beacon floodmode
- WiFi Beacon Jammer
- https://wigle.net
Disclaimer
- Check local WiFi transmission power regulations and set your device's TX power accordingly. Acceptable WiFi TX power varies by country. Specific mW values are listed here though the list may not be up-to-date.